Easy-ELF! Reversing.kr Walkthrough
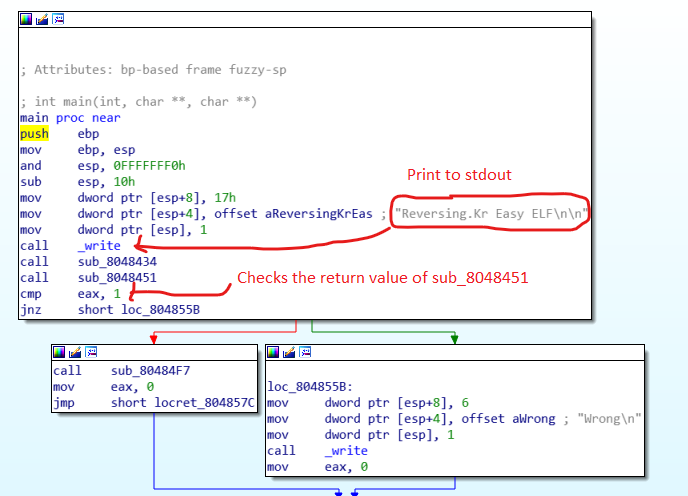
Let’s begin with the main function.
So firstly, the string “Reversing.Kr Easy ELF\n\n” defined in the .data section is printed to stdout.
Further, we can see two function calls – sub_8048434 and sub_8048451. Finally, the return value of function sub_8048451 is checked. If the return value is false, string “Wrong\n” is printed to stdout.
Let’s now proceed to check function sub_8048434. This function reads an input of type string and stores it at address starting from 0x804A020 using “scanf”. As a test scenario let’s consider our input is “xxxxxxx”.
Moving ahead to function sub_8048451. Here we have a series of checks in place. If all the checks are passed, the function returns true or else false. So now let’s analyze each check individually.
In the first case, the 2nd byte of the input is checked to verify weather it is “1”. So now we know, the correct key should be something like “x1xxx..”
Then, in the second case, its checks if the 5th byte of the input is “X”. Moving ahead, The third byte of the input is loaded into eax using movzx instruction.
Looking up the description of movzx, it says “Copies the contents of the source operand (register or memory location) to the destination operand (register) and zero extends the value.” So the lower 8-bits of eax will contain the 3rd byte of the input and the remaining 24 bits will be filled with 0’s. In the next step, eax is XORed with “0110010” and the lower 8-bits of eax (al) is stored at location 0x804A022. Further this value is compared to “1111100”. So here, a xor b = c. The values b and c are known to us we need to perform a reverse xor to get the value of "a".
01111100
00110010
---------
01001110 -> N
We could also conclude that the key is 5 byte long. The 6th byte will be “\n” which will be appended to the string by scanf function.
So know the correct key should be something like “x1NxX”
Performing similar reverse XOR operation, we can find that first byte is “L”. For the 4th byte, the input is XORed with 32-bits but since we are only going to consider the lower 8 bits, we can ignore the later bits. Performing reverse XOR, gives us the 4th byte as “U”.
So now we have the entire key, which is “L1NUX”.
Thank you!!






Comments
Post a Comment