Easy-ELF! Reversing.kr Walkthrough
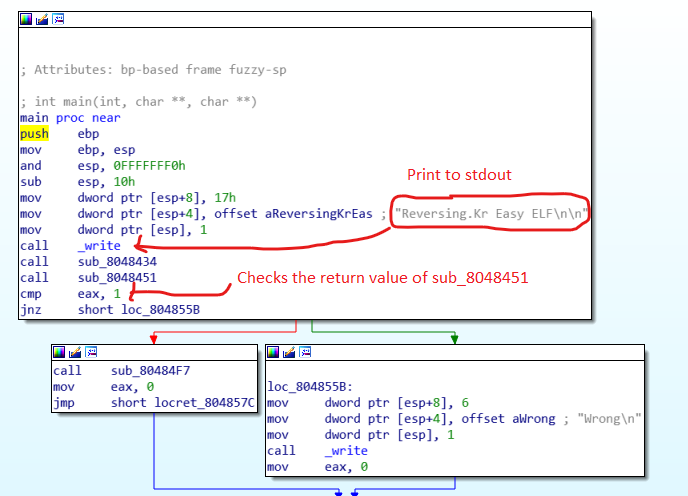
Let’s begin with the main function. So firstly, the string “Reversing.Kr Easy ELF\n\n” defined in the .data section is printed to stdout. Further, we can see two function calls – sub_8048434 and sub_8048451. Finally, the return value of function sub_8048451 is checked. If the return value is false, string “Wrong\n” is printed to stdout. Let’s now proceed to check function sub_8048434. This function reads an input of type string and stores it at address starting from 0x804A020 using “scanf”. As a test scenario let’s consider our input is “xxxxxxx”. Moving ahead to function sub_8048451. Here we have a series of checks in place. If all the checks are passed, the function returns true or else false. So now let’s analyze each check individually. In the first case, the 2nd byte of the input is checked to verify weather it is “1”. So now we know, the correct key should be something like “x1xxx..” Then, in the second case, its checks if the 5 th byte of the input ...