Armageddon - HTB Write-up
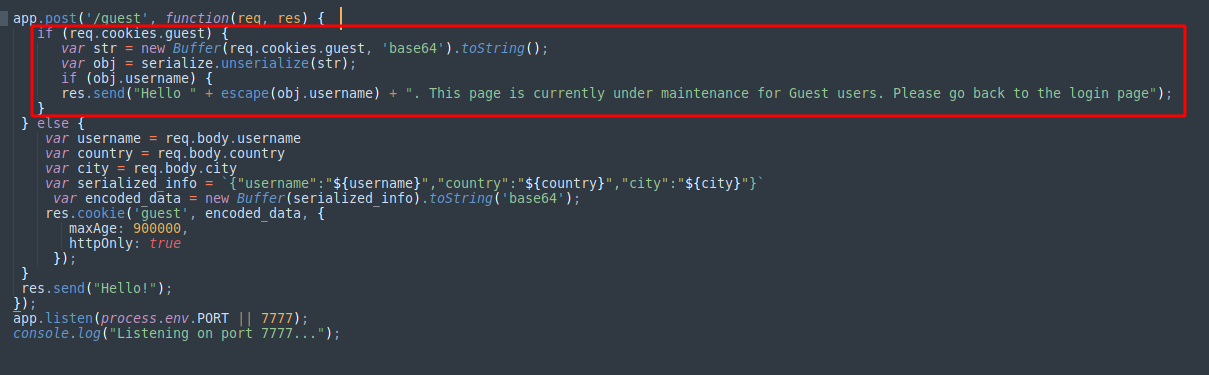
Hello guys! hope you all are doing good. In this blog post, I would like to explain my methodology that I used for pwning the Armageddon box. I hope this would add some educational value for someone who is just starting up with penetration testing. (I am just a wanna be penetration tester. Feel free to point out my mistakes 😜 ) 1.1 Methodology - Information Gathering Lets begin by running a Nmap scan. The nmap scan shows that a web application is running on port 80. On checking the CMS technology in use and its version, I could find that the application is built on Drupal 7. 1.2 Methodology - Initial Foothold Vulnerability Exploited: Drupal 7 CVE-2018-7600. Vulnerability Explanation: A remote code execution vulnerability exists within multiple subsystems of Drupal 7.x and 8.x. This potentially allows attackers to exploit multiple attack vectors on a Drupal site, which could result in the site being completely compromised. Severity: Highly Critical Ref: https://github.com/d...