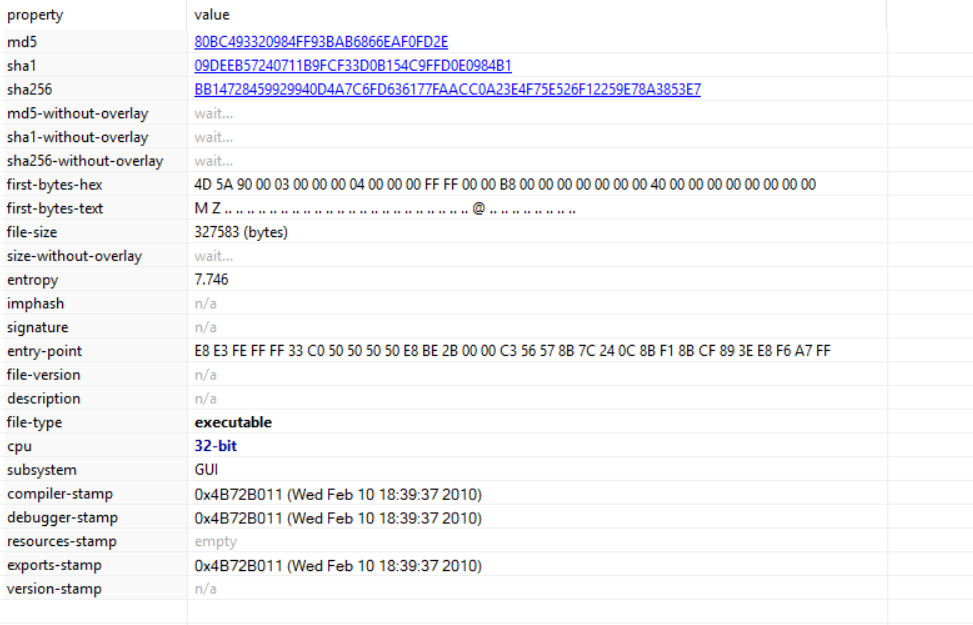
An Overview of SRUM Forensics
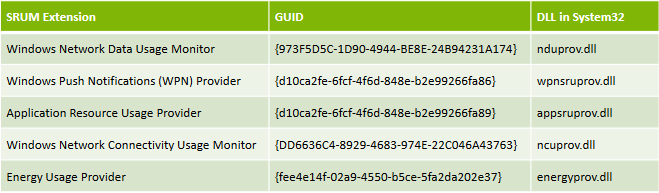
Often there comes a scenario where a malware has run on the host system and there is suspicion of data exfiltration. One forensic technique that comes in handy in such situations is SRUM forensics. Introduction to System Resource Usage Monitor SRUM was first introduced in Windows 8 operating system for keeping a track of system resource usage. In particular, information such as process owner, CPU cycles used by the process, data bytes read/written, network data sent/received, Windows push notifications and energy usage is continuously recorded. SRUM is part of diagnostic policy service and it monitors desktop applications, programs, services, windows applications and network connections. The data that is visualized when one open’s the task manager is part of SRUM data feed. The SRUM data collection happens once in every hour and at shut down. SRUM uses the below extensions for monitoring and data collection. Source: Windows 8 SRUM Forensics - SANS DFIR Summit 2015(Slides) b...